Add Christmass advisories
This commit is contained in:
@@ -0,0 +1,61 @@
|
||||
I’m sharing this with you because your Stella Ops vision for vulnerability triage and supply‑chain context beats what many current tools actually deliver — and the differences highlight exactly where to push hard to out‑execute the incumbents.
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
**Where competitors actually land today**
|
||||
|
||||
**Snyk — reachability + continuous context**
|
||||
|
||||
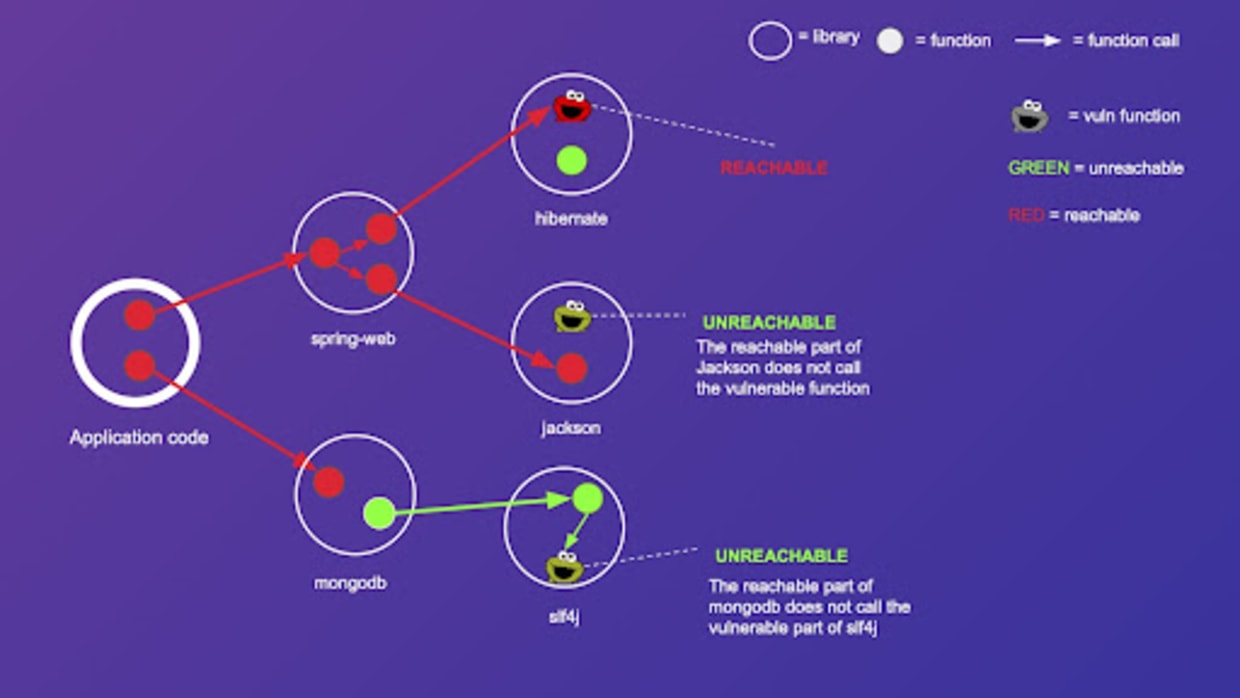
* Snyk now implements *reachability analysis* that builds a call graph to determine if vulnerable code *is actually reachable by your application*. This is factored into their risk and priority scores to help teams triage what matters most, beyond just severity numbers. ([Snyk Docs][1])
|
||||
* Their model uses static program analysis combined with AI and expert curation for prioritization. ([Snyk Docs][1])
|
||||
* For ongoing monitoring, Snyk *tracks issues over time* as projects are monitored and rescanned (e.g., via CLI or integrations), updating status as new CVEs are disclosed — without needing to re‑pull unchanged images. ([Snyk Docs][1])
|
||||
|
||||
**Anchore — vulnerability annotations & VEX export**
|
||||
|
||||
* Anchore Enterprise has shipped *vulnerability annotation workflows* where users or automation can label each finding with context (“not applicable”, “mitigated”, “under investigation”, etc.) via UI or API. ([Anchore Documentation][2])
|
||||
* These annotations are exportable as *OpenVEX and CycloneDX VEX* formats so downstream consumers can consume authoritative exploitability state instead of raw scanner noise. ([Anchore][3])
|
||||
* This means Anchore customers can generate SBOM + VEX outputs that carry your curated reasoning, reducing redundant triage across the supply chain.
|
||||
|
||||
**Prisma Cloud — runtime defense**
|
||||
|
||||
* Prisma Cloud’s *runtime defense* for containers continually profiles behavior and enforces *process, file, and network rules* for running workloads — using learning models to baseline expected behavior and block/alert on anomalies. ([Prisma Cloud][4])
|
||||
* This gives security teams *runtime context* during operational incidents, not just pre‑deployment scan results — which can improve triage but is conceptually orthogonal to static SBOM/VEX artifacts.
|
||||
|
||||
**What Stella Ops should out‑execute**
|
||||
|
||||
Instead of disparate insights, Stella Ops can unify and elevate:
|
||||
|
||||
1. **One triage canvas with rich evidence**
|
||||
|
||||
* Combine static *reachability/evidence graphs* with call stacks and evidence traces — so users see *why* a finding matters, not just “reachable vs. not”.
|
||||
* If you build this as a subgraph panel, teams can trace from SBOM → code paths → runtime indicators.
|
||||
|
||||
2. **VEX decisioning as first‑class**
|
||||
|
||||
* Treat VEX not as an export format but as *core policy objects*: policies that can *explain*, *override*, and *drive decisions*.
|
||||
* This includes programmable policy rules driving whether something is actionable or suppressed in a given context — surfacing context alongside triage.
|
||||
|
||||
3. **Attestable exception objects**
|
||||
|
||||
* Model exceptions as *attestable contracts* with *expiries and audit trails* — not ad‑hoc labels. These become first‑class artifacts that can be cryptographically attested, shared, and verified across orgs.
|
||||
|
||||
4. **Offline replay packs for air‑gapped parity**
|
||||
|
||||
* Build *offline replay packs* so the *same UI, interactions, and decisions* work identically in fully air‑gapped environments.
|
||||
* This is critical for compliance/defense customers who cannot connect to external feeds but still need consistent triage and reasoning workflows.
|
||||
|
||||
In short, competitors give you pieces — reachability scores, VEX exports, or behavioral runtime signals — but Stella Ops can unify these into *a single, evidence‑rich, policy‑driven triage experience that works both online and offline*. You already have the architecture to do it; now it’s about integrating these signals into a coherent decision surface that beats siloed tools.
|
||||
|
||||
[1]: https://docs.snyk.io/manage-risk/prioritize-issues-for-fixing/reachability-analysis?utm_source=chatgpt.com "Reachability analysis | Snyk User Docs"
|
||||
[2]: https://docs.anchore.com/current/docs/vulnerability_management/vuln_annotations/?utm_source=chatgpt.com "Vulnerability Annotations and VEX"
|
||||
[3]: https://anchore.com/blog/anchore-enterprise-5-23-cyclonedx-vex-and-vdr-support/?utm_source=chatgpt.com "Anchore Enterprise 5.23: CycloneDX VEX and VDR Support"
|
||||
[4]: https://docs.prismacloud.io/en/compute-edition/30/admin-guide/runtime-defense/runtime-defense-containers?utm_source=chatgpt.com "Runtime defense for containers - Prisma Cloud Documentation"
|
||||
|
||||
--
|
||||
Note from the the product manager. Note there is AdvisoryAI module on the Stella Ops suite
|
||||
Reference in New Issue
Block a user