audit notes work completed, test fixes work (95% done), new sprints, new data sources setup and configuration
This commit is contained in:
@@ -0,0 +1,29 @@
|
||||
I’m sharing this because it’s a crisp snapshot of how some modern AppSec and supply‑chain tools *feel* in real workflows—where they fit, and what trade‑offs teams bump into as they try to shift left without losing signal or evidence.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
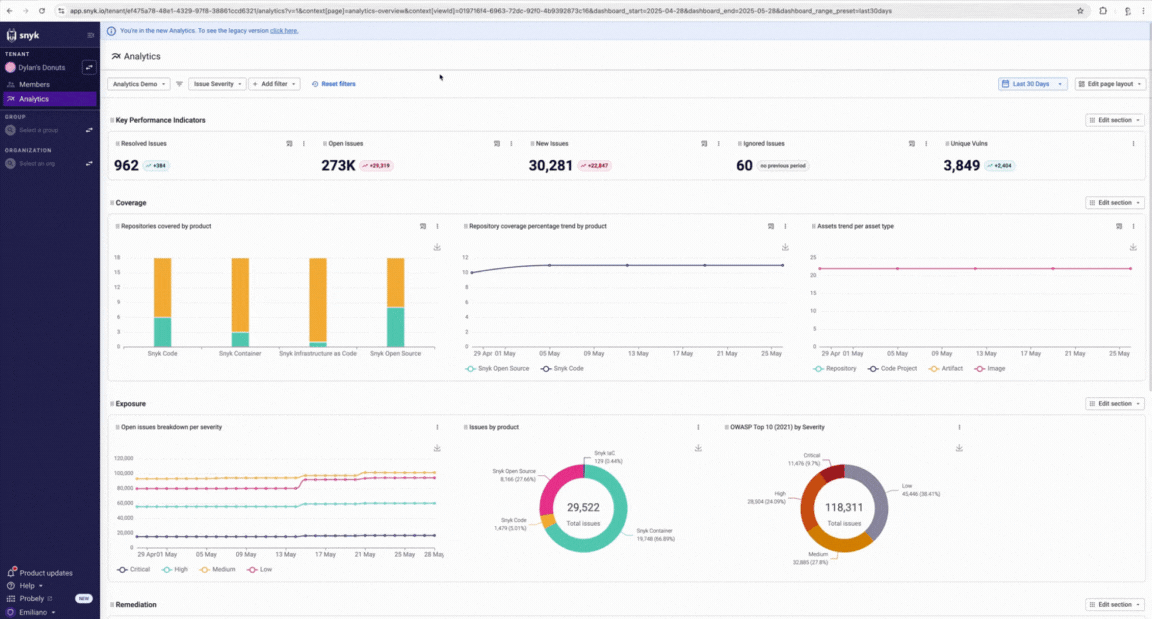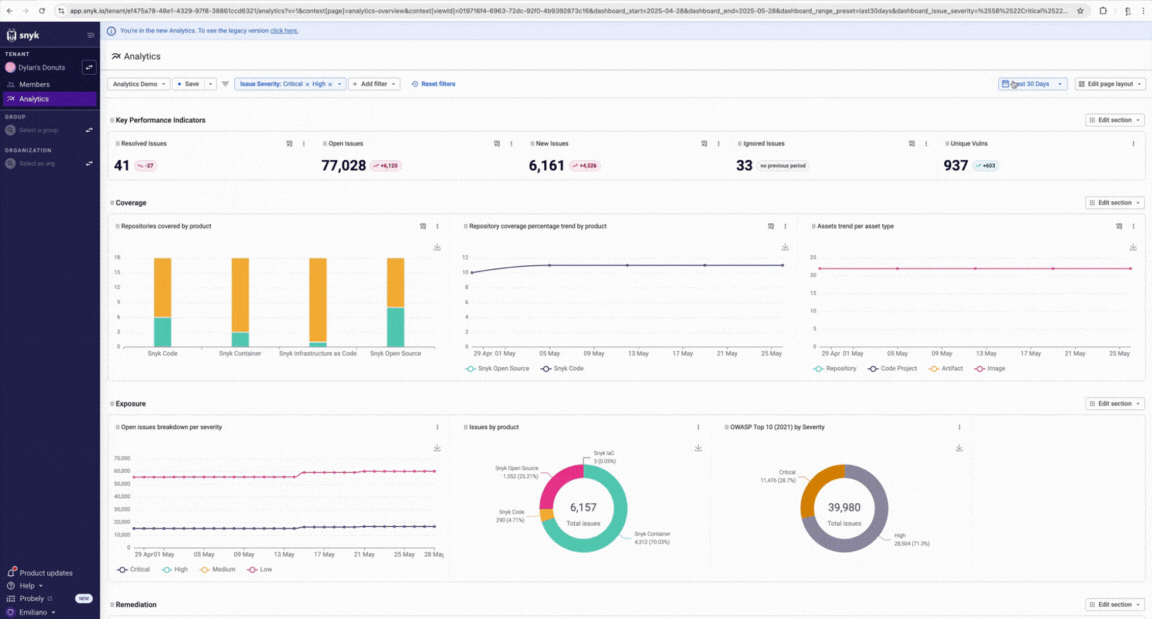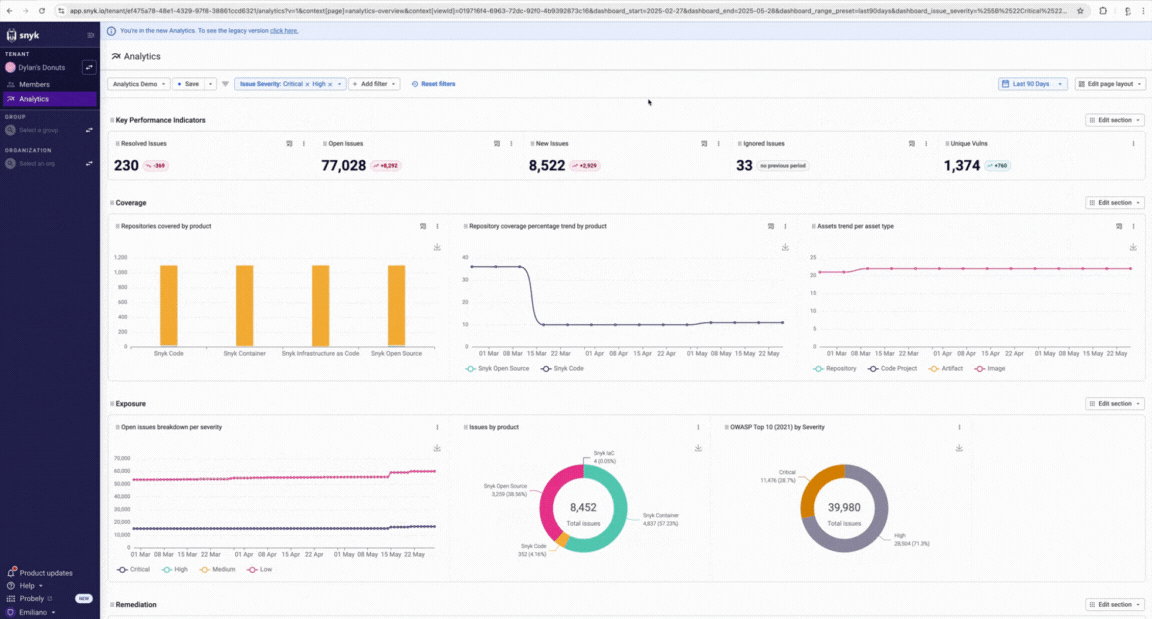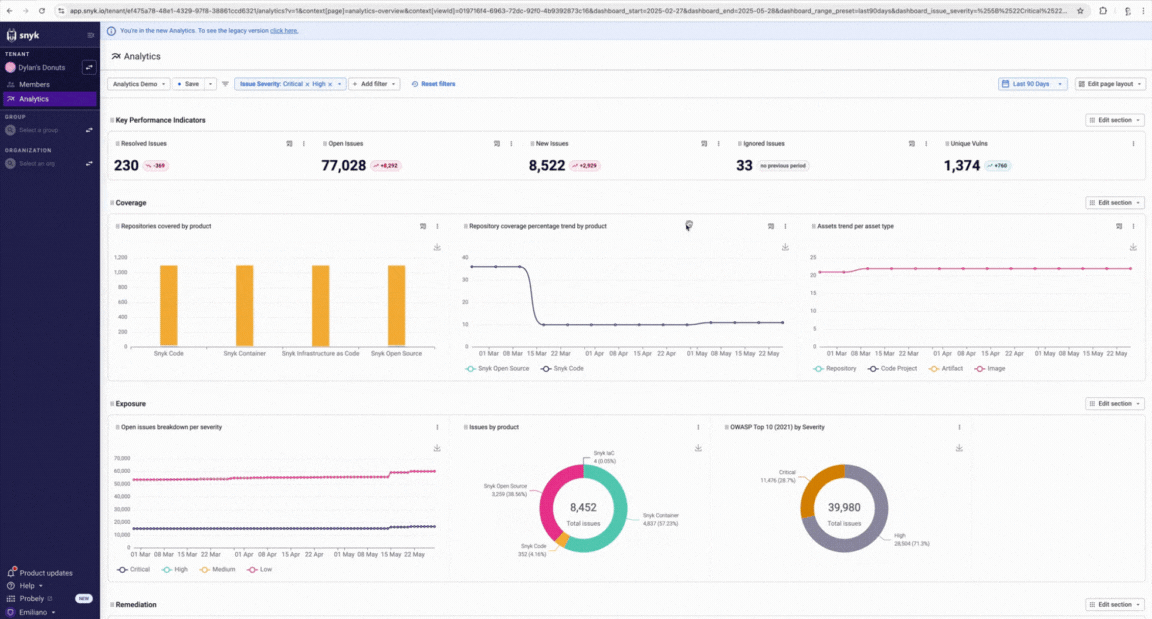
**Snyk** leans hard into developer‑first onboarding and inline feedback early in IDE/CI flows, with rich docs and in‑product training that help catch issues before builds, though it’s still mostly about surfacing textual context and guidance rather than anchored cryptographic evidence about what changed. ([Snyk][1])
|
||||
|
||||
**JFrog Xray** brings deep SCA into the artifact‑centric world of Artifactory, with detailed binary and vulnerability context tied to your repos; it’s strong for repo‑centric enforcement and policy gating, but typical remediation flows are policy or ticket‑oriented rather than built around machine‑verifiable proofs. ([JFrog][2])
|
||||
|
||||
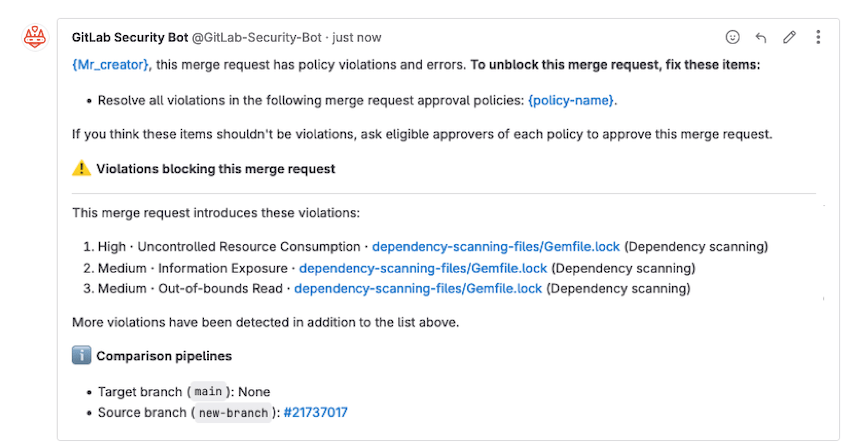
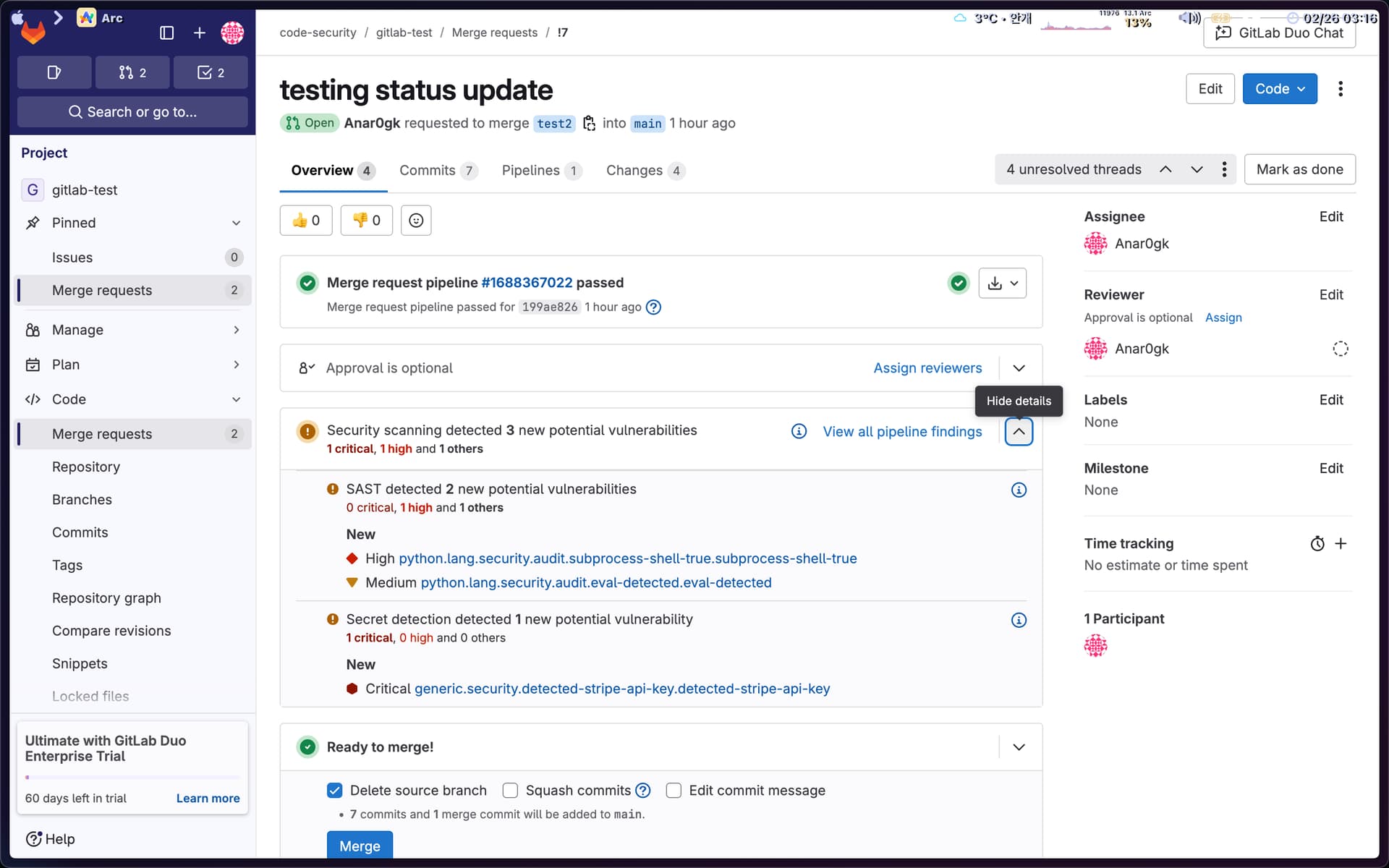
**GitLab’s security scanners** are embedded into its CI/CD and MR experience, showing vulnerability data right in merge requests and making triage visible where devs work; panels tend to prioritize traditional metadata like CVSS and advisory info rather than deterministic proofs or binary diff traces. ([JFrog][3])
|
||||
|
||||
**Aqua Security** scans containers and runtimes across lifecycle stages with rich integrations and AI‑guided remediation suggestions that help push fixes into ticketing/workflows, but such guidance often feels generic without machine‑verifiable evidence of safety. ([strongdm.com][4])
|
||||
|
||||
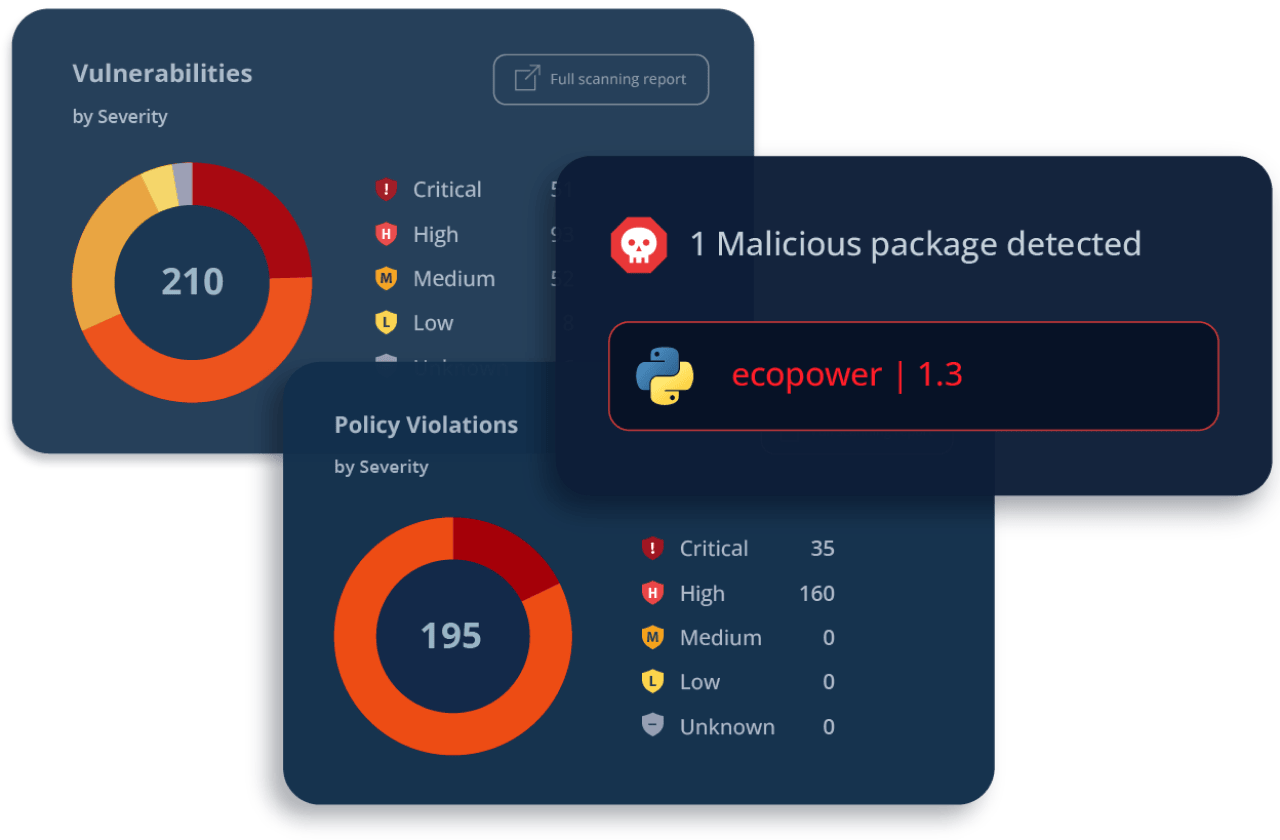
**Anchore’s open tools (Syft & Grype)** are SBOM‑first: Syft generates detailed bills of materials, Grype scans them for vulnerabilities; they excel at inventory and actionable plans but their UIs and workflows don’t inherently include cryptographic attestations or tight evidence‑anchored remediation flows. ([Anchore][5])
|
||||
|
||||
Each of these tools is useful in its niche, but the subtle differences in how they onboard devs, present context, and *anchor evidence* matter a lot when you’re aiming for deterministic, supply‑chain‑proof workflows.
|
||||
|
||||
[1]: https://snyk.io/articles/developer-first-security/?utm_source=chatgpt.com "Developer-First Security"
|
||||
[2]: https://jfrog.com/help/r/jfrog-security-user-guide/products/xray?utm_source=chatgpt.com "Xray"
|
||||
[3]: https://jfrog.com/jfrog-vs-gitlab/?utm_source=chatgpt.com "JFrog vs GitLab Comparison"
|
||||
[4]: https://www.strongdm.com/blog/devsecops-tools?utm_source=chatgpt.com "8 DevSecOps Tools for Modern Security-First Teams in 2026"
|
||||
[5]: https://anchore.com/opensource/?utm_source=chatgpt.com "Open Source Container Security with Syft & Grype"
|
||||
Reference in New Issue
Block a user